- Mail:
- info@digital4pro.com
IoT: Long range and low power connections with LoRaWAN

IoT: Connessioni a lungo raggio e bassa potenza con LoRaWAN
1 Luglio 2020
Sport: Elena e Marina Compagnoni, Owners Celso Sport
2 Luglio 2020Summary
The concept of the Internet of Things (IoT), provides for the interconnection of various intelligent physical objects (things), such as sensors and actuators, also making them accessible via the Internet and thus creating a closer integration between physical space and digital space (cyberphysical system). This requires communication systems with wide coverage, low service costs, and high energy efficiency, as peripheral devices are often battery powered.
Low Power Wide Area Network (LPWAN) technologies were born to try to meet this need, allowing peripheral nodes to transmit data via radio over distances of a few kilometers, even in hostile environments, with very low energy consumption.
Among the various LPWAN technologies developed in recent years, of particular interest is the Long-Range Wide Area Network (LoRaWAN) system, promoted by the LoRa Alliance which, to date, has over 500 companies and international organizations1.
In a few years, LoRaWAN technology has managed to gain a significant market share, stimulating the creation of a strong ecosystem, with partners who develop different parts of the system and integrators who sell complete solutions for both geographic and residential / industrial networks.
At the basis of this success there are some interesting technical characteristics and the possibility of configuring some network parameters in order to adapt the functioning of the system to the specific operating context, thus improving energy efficiency and capacity. The following of this article will illustrate in more detail the most significant technical aspects of the LoRaWAN system, referring to the technical specifications for a detailed analysis.
Network architecture
The architecture of a LoRaWAN system is schematically represented in Figure 1. The system consists of three main elements, namely: peripheral nodes, usually sensors or actuators; one or more gateways; and a Network Server. The peripheral nodes exchange data exclusively with the gateways via LoRa radio modulation. The gateways, in turn, are connected by means of legacy Internet technologies (IP) to the Network Server. The latter takes care of the management of the entire system: sets the configurable parameters, receives data from peripheral nodes (via the gateways) and forwards them to server-side applications and vice versa (always through the gateways), and so on.
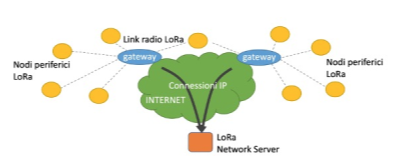
Figura 1 – Architettura di un sistema LoRaWAN.
Note that the transmissions of the peripheral nodes are not addressed to a particular Gateway, but are received and forwarded to the Network Server by all the Gateways within the transmitter’s coverage range. This greatly simplifies network planning and allows to increase the robustness of uplink transmissions (from peripheral nodes to the network) by placing a greater number of gateways in the area to be covered. Duplicate packets are discarded by the Network Server, which uses meta-information transmitted by the Gateways (for example, the strength of the signal received) to choose the Gateway to be used for any response messages to peripheral nodes
LoRa modulation, transmission speed, and coverage rays
Radio communication is based on LoRa modulation, whose patent is held by the Semtech company.
LoRa uses a chirp spread spectrum technique which consists in the transmission of a sinusoidal signal with increasing frequency in the symbol period, with a ramp up in frequency that depends on the symbol to be sent2.
The transmission speed depends on the spreading factor (SF), a configurable parameter that can vary from 7 to 12: low SF values correspond to higher data transmission speeds, but require greater signal strength to the receiver for correct decoding, which results in shorter coverage radii.
Table 1 shows some indicative values of transmission speed and coverage rays for the various SFs for a probability of error on the packet of less than 1%, considering the frequency band not licensed at 868 MHz in which the system operates in Europe, with 125 kHz channel width, and 4/5 coding rate.
.
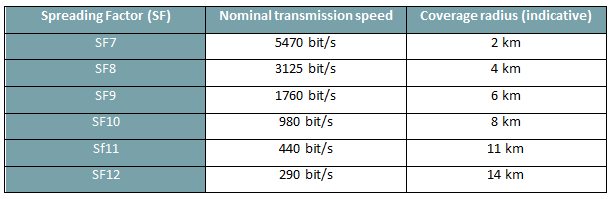
Tabella 1 – Velocità di trasmissione e raggi copertura per i diversi SF.
It should be noted that signals transmitted with different SF are almost orthogonal, that is, they can be decoded without errors even if they overlap in time and frequency, provided that the powers of the two signals are sufficiently distant3.
Many commercial gateways exploit this property by implementing several parallel reception chains that allow to receive as many signals simultaneously. However, gateways cannot transmit and receive simultaneously. In addition, the system must comply with the limitations provided for in the CEPT 70-03 recommendation which imposes an average ratio between the transmission and silent periods of a device (duty cycle) that varies between 0.1% and 10% depending on the sub-bands considered. This constraint, often implemented at the firmware level at each individual transmission (when, on the other hand, regulations require compliance with the duty cycle on average over a time interval of one hour), can lead to high latencies if it is necessary to transmit several packets in rapid succession ( for example, for a software update, or in case of reporting of anomalous events).
Network performance
The performance of LoRaWAN networks has been studied extensively in the literature in recent years4.
Most studies assume uplink-only traffic, focusing on pure monitoring scenarios. Based on these assumptions, LoRaWAN has proven to be able to support hundreds of devices, distributed over an area of several square kilometers, which generate traffic with inter-packet periods ranging from 30 minutes to 24 hours, for traffic aggregate up to 0.8 packets/s, with a reliability of about 95% with a single Gateway. The system capacity can be further extended by distributing multiple gateways and / or by adopting intelligent strategies to assign SFs to different peripheral nodes.
The presence of downlink traffic, that is, from the network to the peripheral nodes (including the control traffic generated by the NetworkServer in the event of the transmission of “confirmed” packets by the peripheral nodes), can significantly impact the system capacity. In fact, it has been observed that, in scenarios where nodes can send both “confirmed” and “unconfirmed” packets, the latter have a higher probability of not being delivered due to the inability of the Gateways to receive and transmit simultaneously . However, some of these inefficiencies can be mitigated by suitably changing the system settings.
Security
LoRaWAN uses two levels of security: one for the network, which guarantees the authenticity of the node in the network, and one at the application level that ensures that the network operator does not have access to the data of the end user application. An AES encryption with key exchange is used. Pairing between the device and the network can occur in two different ways: Over-The-Air Activation (OTAA), which allows you to establish a session key with the servers, and Activation By Personalization (ABP), a manual procedure for installing the keys which, however, does not allow the keys to be regenerated periodically, and therefore is not recommended.
Conclusions
From this analysis we can conclude that LoRaWAN helps to fill a gap in the arena of wireless communication technologies, providing a very flexible, secure, energy efficient, easy to implement and relatively low cost way to connect a multitude of nodes. with low traffic demand.
To date, the LoRaWAN commercial offer boasts many LoRa-compliant peripheral devices, and makes it possible to create completely private networks, through the purchase and management of gateways and network servers, and to access the service in platform mode -as-a-service, in which the construction and management of the network is delegated to an operator, who then redirects communications to the client’s application servers.
As a final consideration, we note the lack of a clearly predominant technology in the LPWAN arena is causing a slowdown in the adoption of these technologies. However, a working group of the Internet Engineering Task Force (IETF) is developing a protocol compression protocol called SCHC (pronounced “chic”), which allows IPv6 connectivity also in LPWAN networks, paving the way for a effective interoperability between them and with other solutions, such as NB-IoT.
1 L. Vangelista, A. Zanella, and M. Zorzi, “Long-range IoT technologies: The dawn of LoRaTM,” in Future access enablers of ubiquitous and intelligent infrastructures. Springer, 2015, pp. 51-58
2L. Vangelista, “Frequency shift chirp modulation: the LoRa modulation,” IEEE Signal Processing Letters, vol. 24, no. 12, pp. 1818–1821, Dec. 2017.
3D. Croce, M. Gucciardo, S. Mangione, G. Santaromita, and I. Tinnirello, “Impact of LoRa Imperfect Orthogonality: Analysis of Link-Level Performance,” IEEE Communications Letters, vol. 22, no. 4, pp. 796–799, 2018.
4D. Magrin, M. Capuzzo, A. Zanella. “A Thorough Study of LoRaWAN Performance Under Different Parameter Settings,” IEEE Internet of Things Journal vol. 7, no. 1, pp. 116-127, Jan. 202
Bibliography:
- L. Vangelista, A. Zanella, and M. Zorzi, “Long-range IoT technologies: The dawn of LoRaTM,” in Future access enablers of ubiquitous and intelligent infrastructures. Springer, 2015, pp. 51-58.
- L. Vangelista, “Frequency shift chirp modulation: the LoRa modulation,” IEEE Signal Processing Letters, vol. 24, no. 12, pp. 1818–1821, Dec. 2017.
- D. Croce, M. Gucciardo, S. Mangione, G. Santaromita, and I. Tinnirello, “Impact of LoRa Imperfect Orthogonality: Analysis of Link-Level Performance,” IEEE Communications Letters, vol. 22, no. 4, pp. 796–799, 2018
- D. Magrin, M. Capuzzo, A. Zanella. “A Thorough Study of LoRaWAN Performance Under Different Parameter Settings,” IEEE Internet of Things Journal vol. 7, no. 1, pp. 116-127, Jan. 2020




